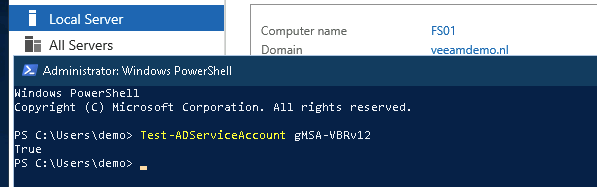
It has been a while since my last post but I finally found some time to write a new one. This time it will be about Veeam Agent for Windows v6 (which is beta) with backups going directly to Object Storage (yes! agents that will directly backup to S3 without the need for anything else).
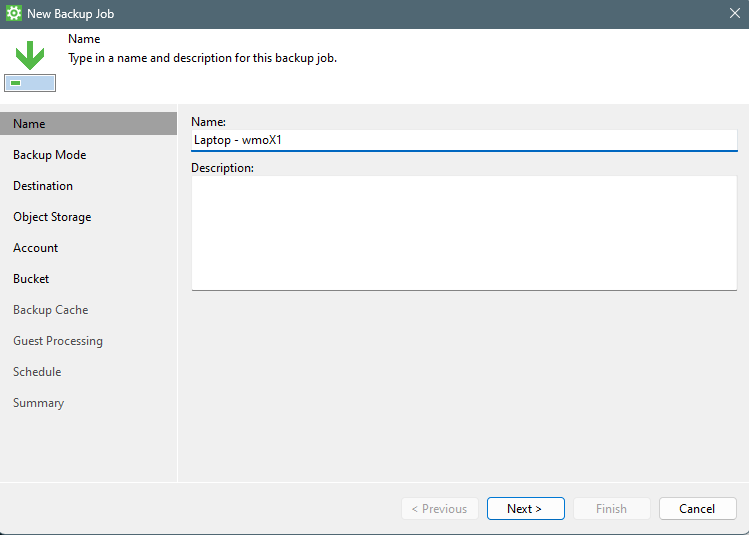
When configuring a job you will get the same questions as with previous versions of the agent. So give it a name.
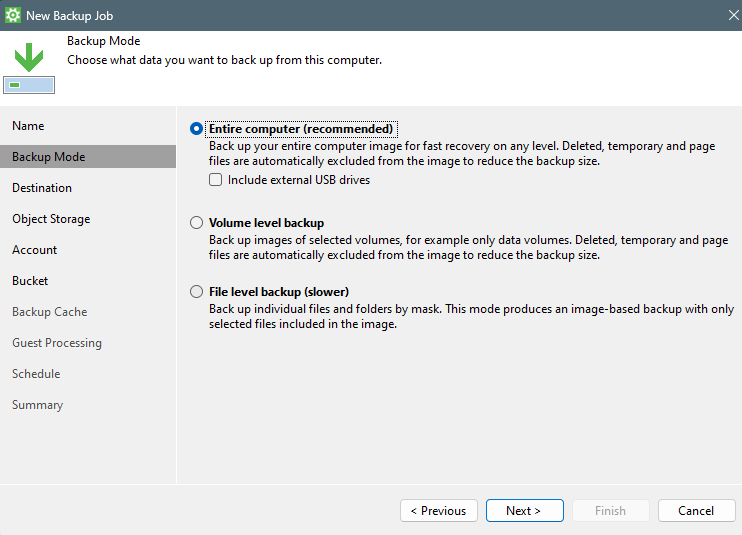
Select what you want to backup, in my case my complete laptop.
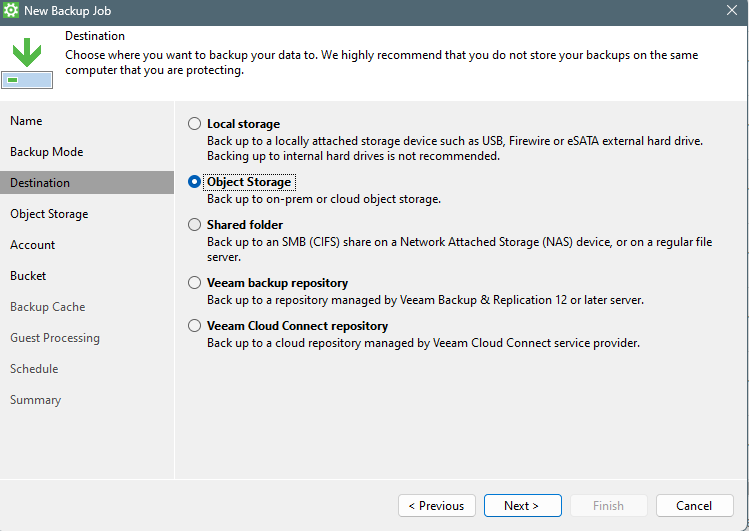
Now for the destination, you can select to use “Object Storage”. This can be either on-premise S3-compatible object storage OR cloud object storage.
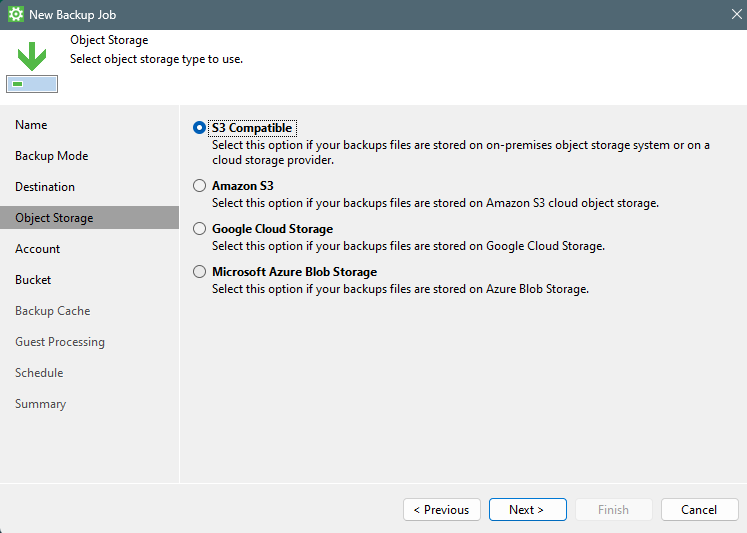
In my case, I select S3 Compatible because I will be using Wasabi.
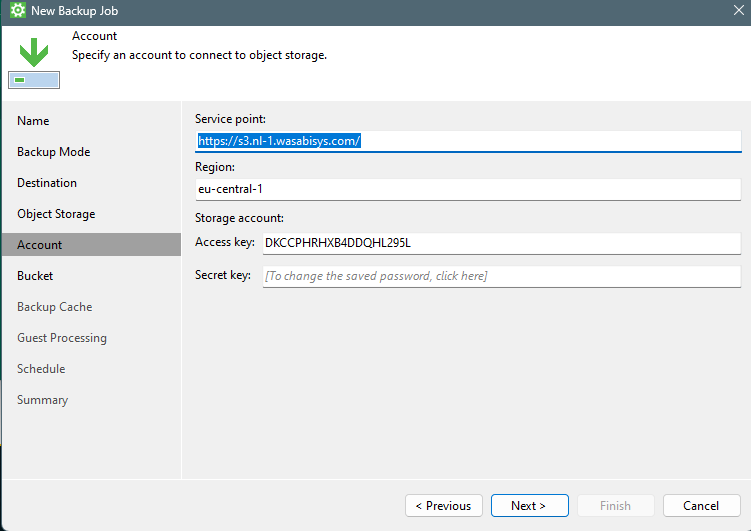
Give in the specifics to connect to the object storage like “service point URL”, “Region” and of course “Access key and Secret key”.
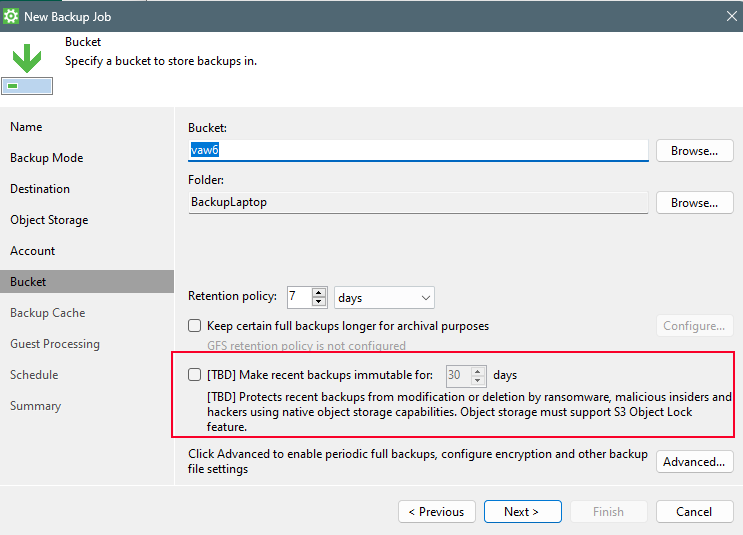
Now….this part is very important! You can even select to use Immutability (S3 Object Lock).
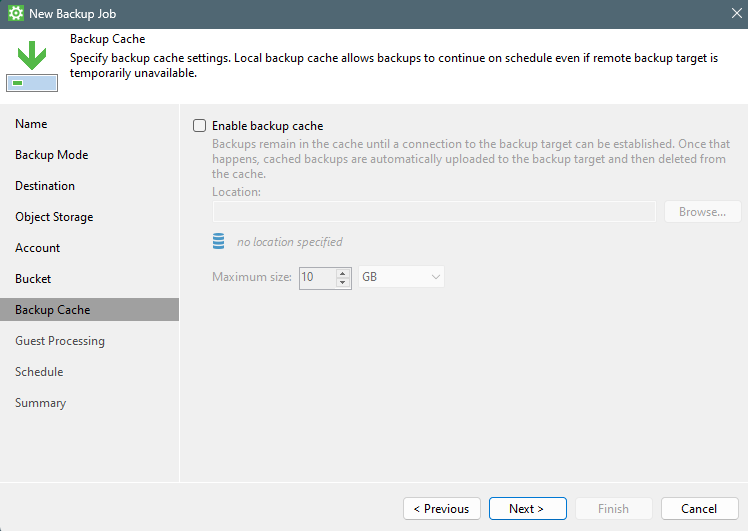
Continue the wizard with the general questions like the “backup cache”.
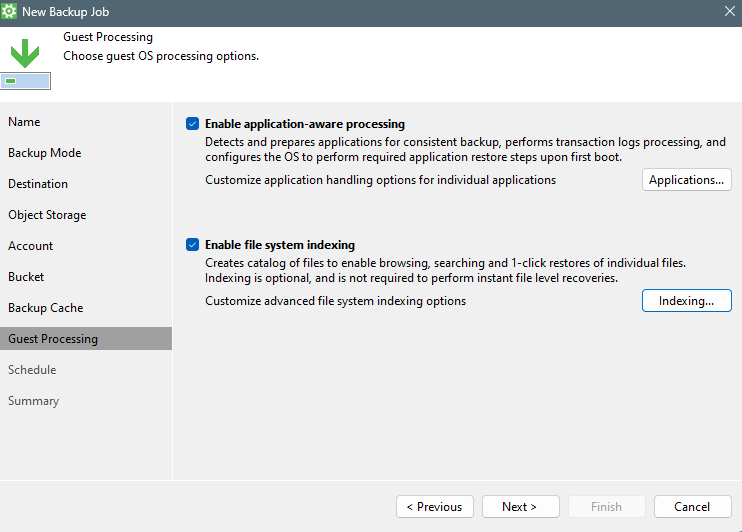
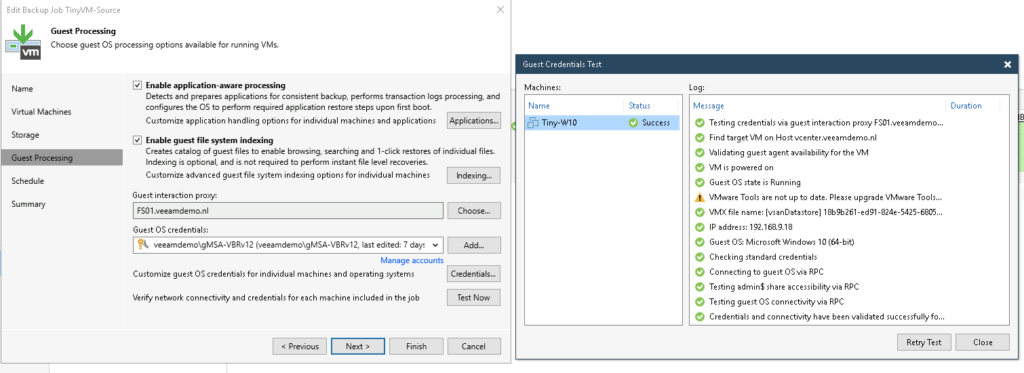
Select if you want to use “Application-aware processing” and/or “File system indexing”.
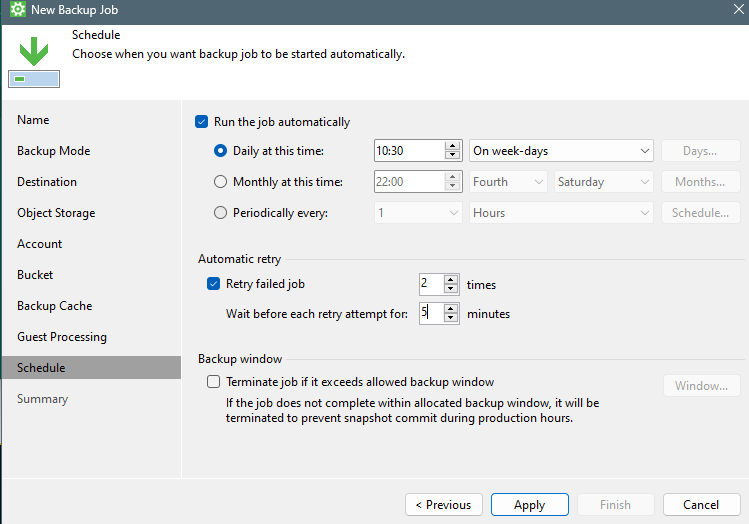
And of course schedule your backups 🙂
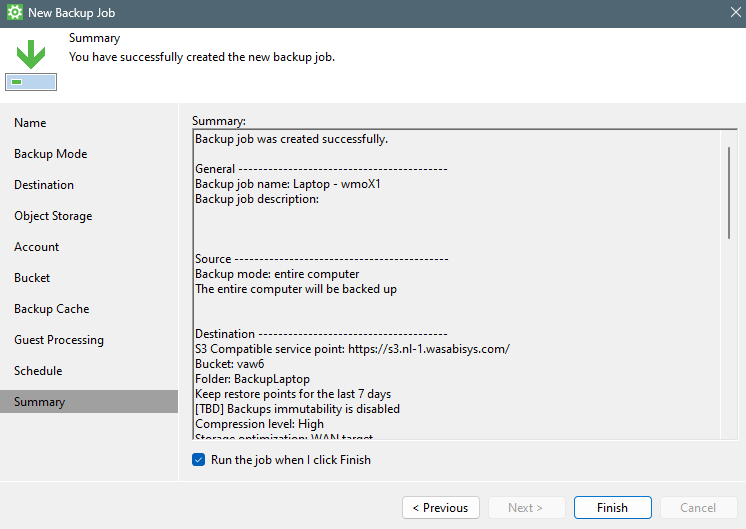
As the final step select to “run the job when I click finish” and click finish.
Now you will see that the backup will go directly to Object Storage!!!